Our security framework
- Rules
The golden rules for ensuring a secure remote connectivity experience. - Configurations
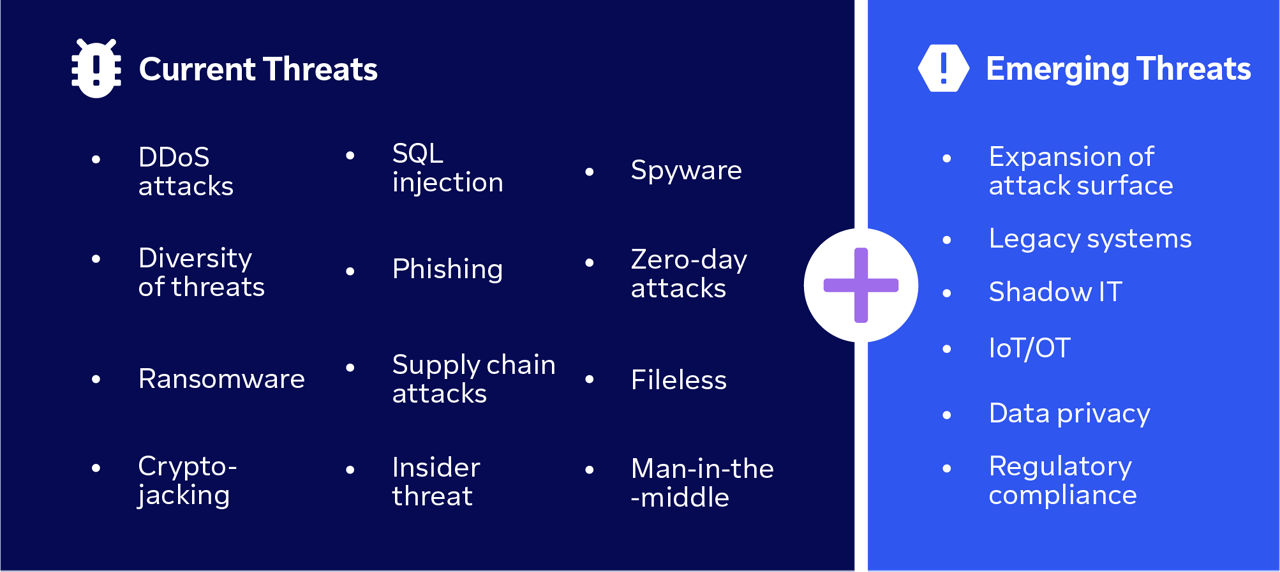
Configuration parameters that involve security in general. - Risks
Potential risks that need to be safeguarded against. - Actors
The actors involved in or affected by security breaches. - Expectations
Setting expectations for a more secure remote connectivity experience. - Commitments
Establishing an organization-wide security posture.